Sometimes it can be necessary to have nasadmin privileges on a VNXe in order to set specific parameters. EMC support should be able to help with this, but sometimes you can not get help from support or you do not want to wait for support.
Here is a guide on how to get nasadmin and root privileges.
You will need:
- Physical access to the VNXe
- Serial cable with micro-DB9 plug (it should have come with the VNXe)
In order to get nasadmin and root privileges we need to reboot each Storage Processor (SP) and enter single-user mode. Figure out which SP you want to reboot first and connect the serial cable to the serial port marked with a small wrench. Connect the other end to your computer and open a terminal like HyperTerm, Tera Term or even Putty. The settings are:
- 9600 baud
- 8 data bits
- no parity
- 1 stop bit
Press [enter] once or twice untill you get a prompt.
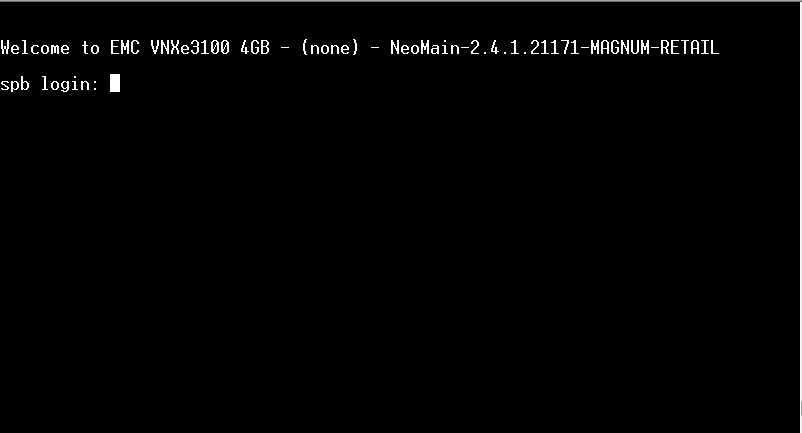
Ensure that you can log in with the service user. We are going to give the nasadmin user the same password as the service user have so you need to know your service password.
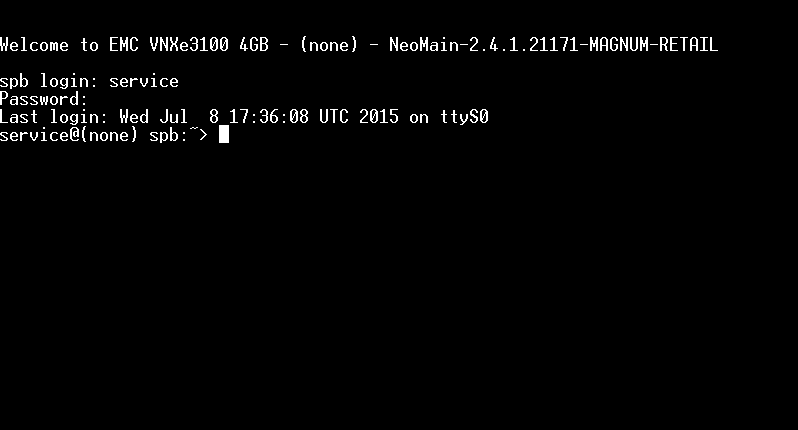
Now that we know we have the serial connection in place we can reboot the SP. You can either do this from the VNXe webinterface (in the service menu) or you can do it from the console you are allready logged in.
To reboot the SP from the CLI you have to issue the following command:
svc_shutdown --reboot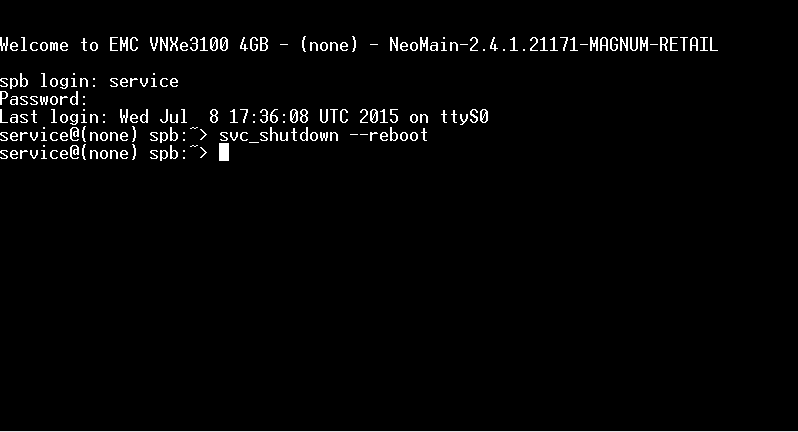
When you have initiated the reboot of the SP, you need to keep an eye on the progress because you need to press [tab] at a point to pause the boot of the system in order to tell that you want to boot in single-user mode. Below are a series of screenshots from a reboot:
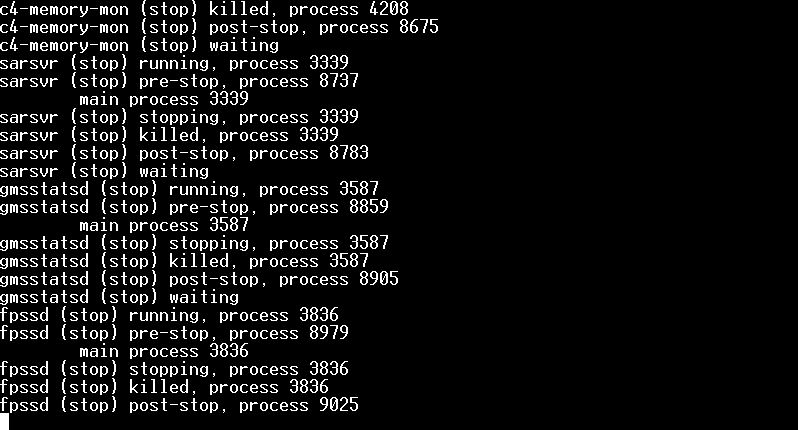
To begin with, you will see a lot of information about services being stopped and so on.
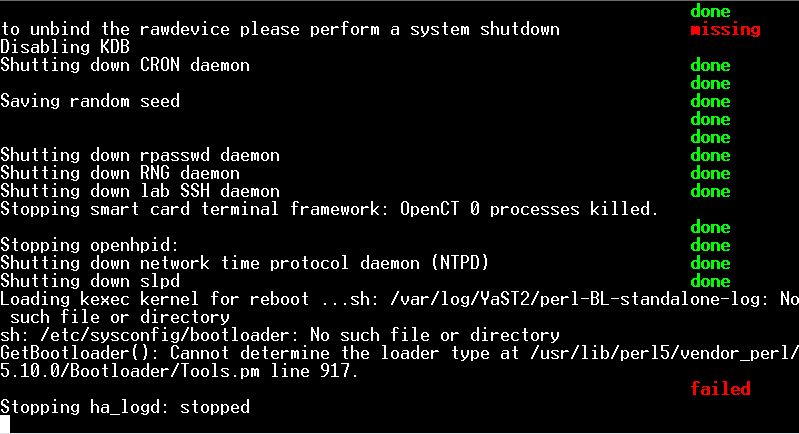
You will also see errors and warnings – You can ignore these
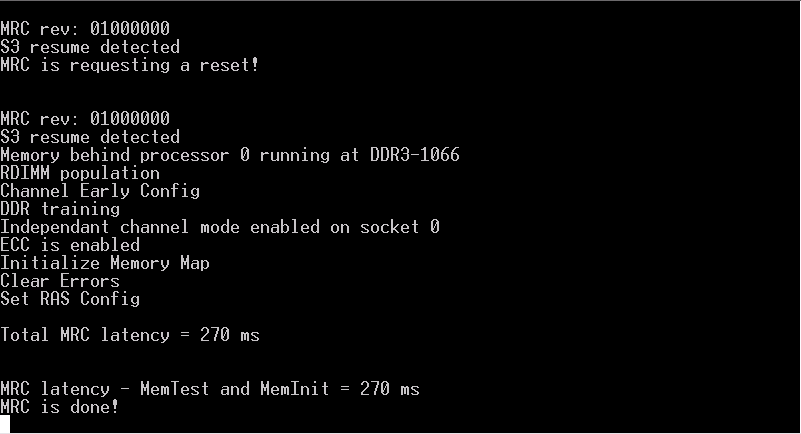
This is the first that is displayed after the reboot
First NIC is initialized
Second NIC is initialized
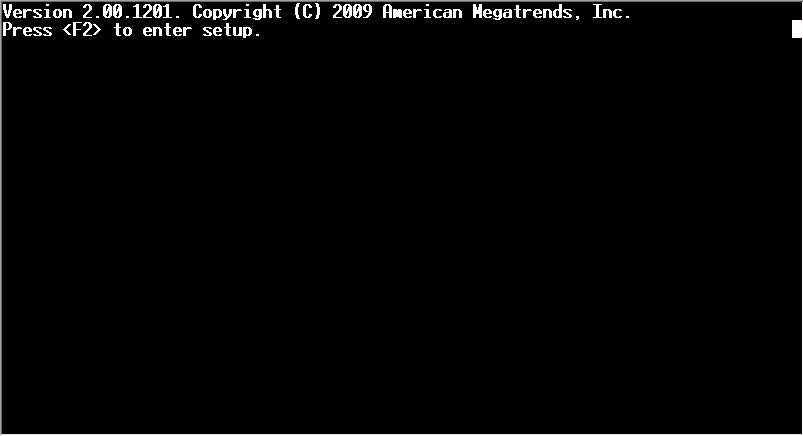
BIOS prompt (I have not been able to send F2 through the serial cable)
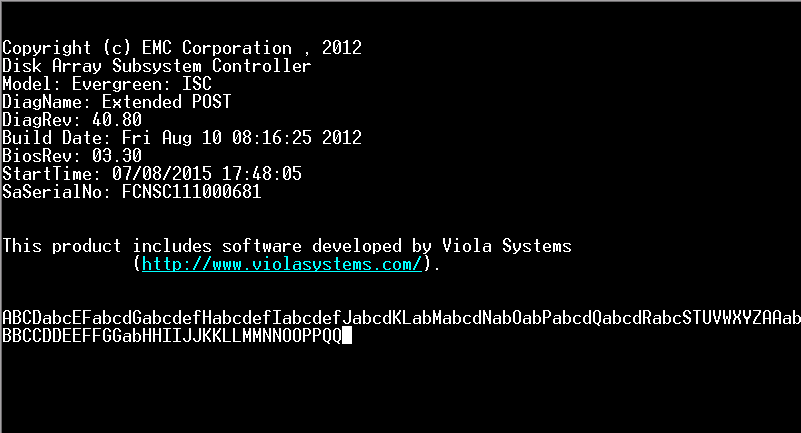
Above shows the progress of some EMC POST tests
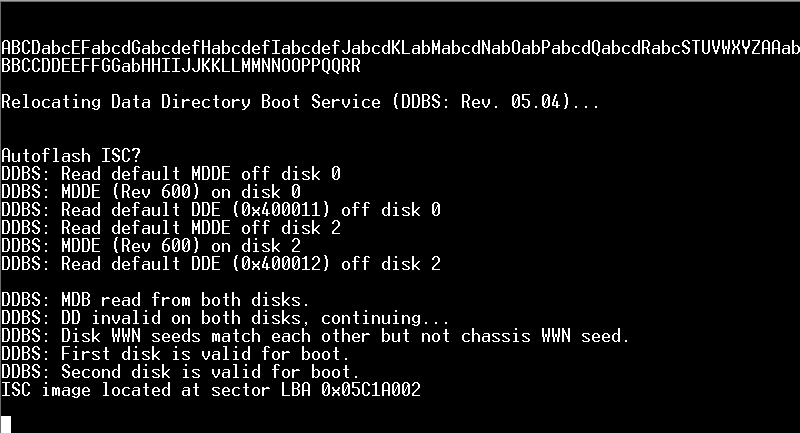
Above is the last thing that is displayed before you have to press [tab]. I usually start pressing the [tab] button regulaly untill I see that I have paused the boot
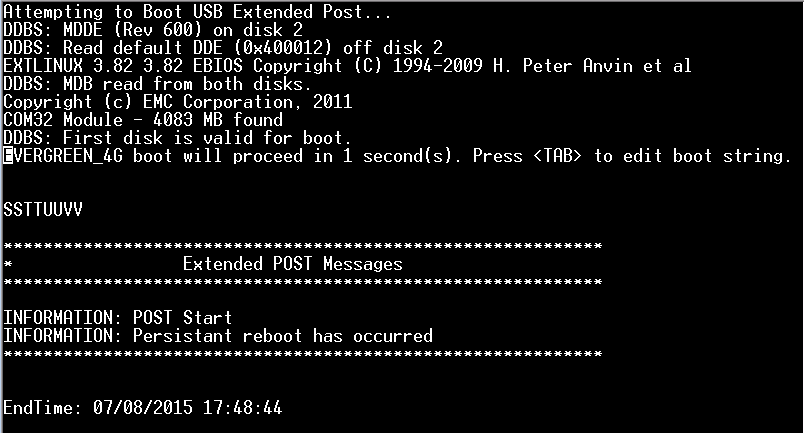
When you see above, you need to be quick about pressing the [tab] button.
After you have successfully pressed [tab] to pause the start of the system, you should see something similar to below:
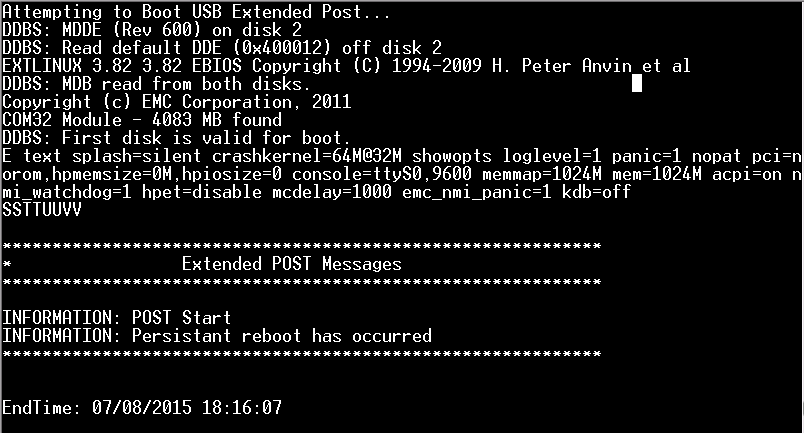
Unfortunately things are a bit scrambled and in the beginning I was not even sure that I had done it correctly. It turns out that this is what it looks like in the serial console and now all you have to do is append the following and press [enter]
init=/bin/sh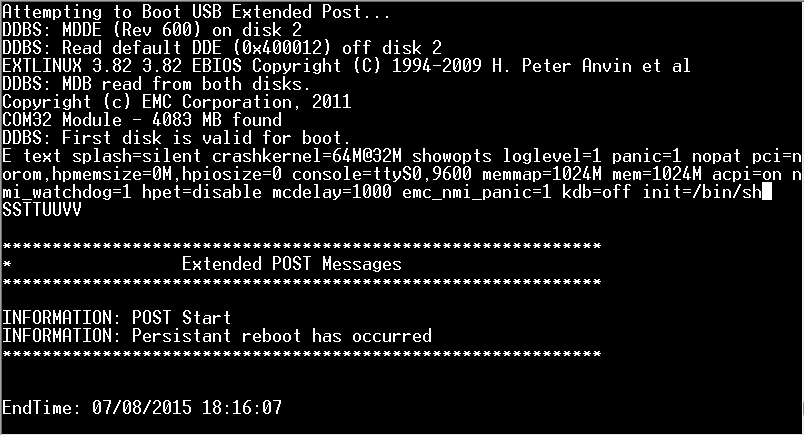
When you have pressed [enter] you should see the kernel being loaded.
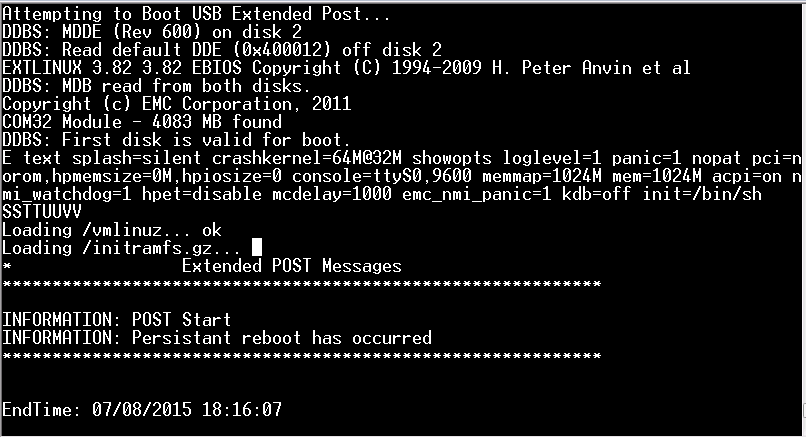
Loads of information will pass by on the console, but after 2-3 minutes you should end up with a prompt.
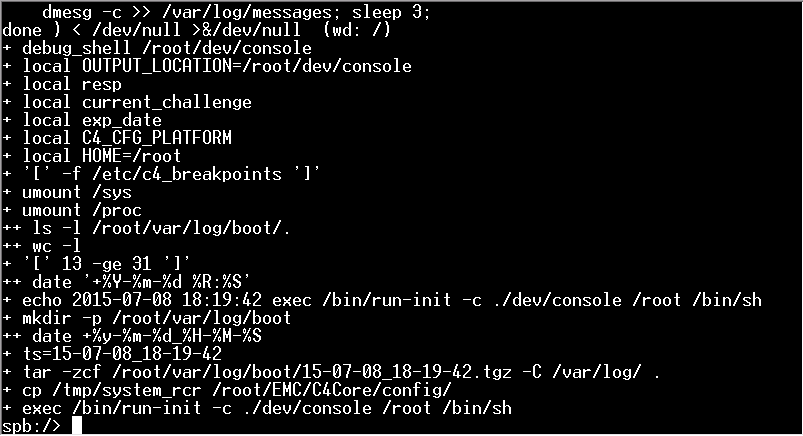
You now have full root access to the SP however it is definitely not everything that works.
I have found that if you do things too quickly, the SP will re-image it self when you reboot into normal mode and all your changes will be lost. If that happens you will have to do it all over again. Take your time and go through the commands at a steady pace.
In order to do as little harm to the system as possible, I chose to just copy the password hash from the service user to the nasadmin user.
First you need to make the /etc/shadow file writeable.
chmod 600 /etc/shadowThen you can edit the file.
vi /etc/shadowI will not go into how to use vi, you can look that up somewhere else, I will just tell you that you need to copy the password hash from the service user to the nasadmin user. The entries in /etc/shadow look something similar to this:
service:$2a$10$M0xluSLD4YeweX9/ugdYvXTeYsZxo4AANbkyKQEsYjtAVlhm:16618:0:9999:7:::
nasadmin:$1$sdlktjxlv.delkjdhgSDKGsdkSFksjfS:16618:0:99999:7:::You need to replace the red text with the green text.
When you have edited and saved /etc/shadow, you need to make it read-only again
chmod 400 /etc/shadowNext, some of the server_* commands that nasadmin can run, actually also need root privileges so you need to ensure that nasadmin can use the sudo command and it might also be a good idea to let the service user run sudo commands. Run the following command to edit /etc/sudoers
visudoAt the end of the file, add the following two lines.
service ALL=(ALL) NOPASSWD: ALL
nasadmin ALL=(ALL) NOPASSWD: ALLThis will allow both the service and the nasadmin user to run commands with root privileges without giving any password, otherwise they would have to provide the root password to run commands with root priviliges.
Last thing before we reboot the SP into normal mode is to ensure that the changes have actually been saved.
cat /etc/shadow
cat /etc/sudoersCheck to output of both commands to ensure that your changes to the files are saved.
Last thing is to reboot into normal mode. Unfortunately we can not do a normal reboot of the system so we need to force it.
reboot -fThe SP should now reboot normally, but now you know the password for the nasadmin user and the service user should be able run sudo commands without being asked for root password.